M09 IPv4 Network Address Translation
Lecture Videos
Address Classes
As previously mentioned under IPv4 Addresses, Subnetting and ARP, the IPv4 address space is divided into private and public addresses. It is easier to remember the private address spaces, and think of the rest as public.
The private address spaces are as follows
- 10.0.0.0 - 10.255.255.255 (10.0.0.0/8)
- 172.16.0.0 - 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 - 192.168.255.255 (192.168.0.0/16)
Very often consumers recognize the 192.168.0.0/24 address space (or something around 192.168.x.0/24) as it is very commonly used in consumer hardware.
The good thing is that these addresses can be reused again and again as long as they are Network Address Translated - NATted to the public Internet!
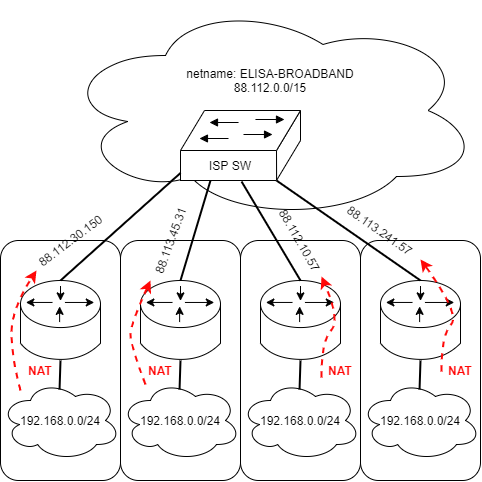
The figure below demonstrates the reusability of the address space.
All the different home routers have 192.168.0.0/24 behind them, but all of them are Network Address Translated to a different public IPv4 address given by the ISP (Elisa in this case as an example). Note that there are 254 different possible private addresses (192.168.0.1 - 192.168.0.254) that are translated to 1 public IPv4 address.
The rule still applies to all of the IP addresses in 192.168.0.0/24. This is called Many-to-1 NAT.
Next we go through the different NAT types and how to configure them on Vyos.
Configuring NAT
Many-to-1 NAT
As stated earlier, the basic and most common implementation of NAT is Many-to-1 NAT.
It means that many consumer devices are hid behind one address and thus conserve the public address space.
Configuring Many-to-1 NAT
The configuration is quite straigth-forward.
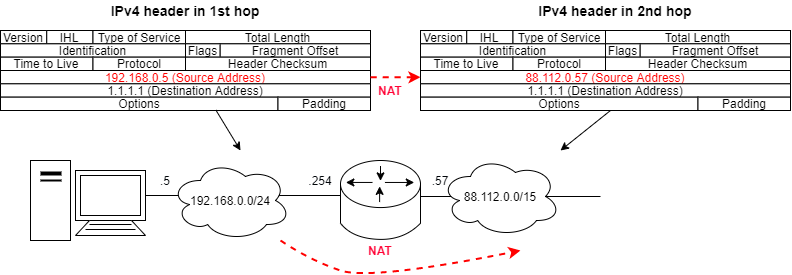
We need to know the interface with the public IPv4 address. This is declared as the outbound-interface and IPv4 packets are masquaraded into that interfaces IPv4 address.
set nat source rule 10 outbound-interface eth0
set nat source rule 10 translation address masquerade
Then we need to have the source IPv4 addresses declared which are translated/masquaraded.
set nat source rule 10 source address 192.168.0.0/24
Given that the outbound-interface has an IPv4 address of 88.112.0.57 the addresses from subnet 192.168.0.0/24 (254 addresses) are all translated to that singular public IPv4 address.
Verifying Many-to-1 NAT with show commands
show nat source translations
vyos@vyos:~$ show nat source translations
Pre-NAT Post-NAT Prot Timeout
192.168.0.5 88.112.0.57 icmp 29
vyos@vyos:~$
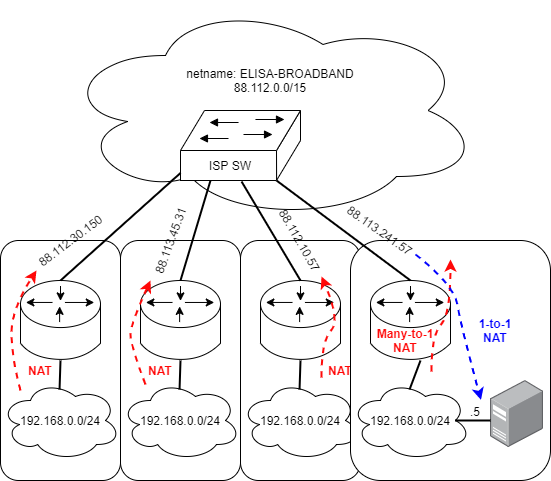
1-to-1 NAT
Sometimes it is necessary to translate the public address back to the private address. To expose e.g. a web server behind the NAT in the local area network. In the example below, connections from the public Internet to address 88.113.241.57 are translated to the private IPv4 address of 192.168.0.5.
Now all the different TCP and UDP ports are translated to that one address. Further firewall rules might be required to limit this tcp/udp port space. TCP and UDP are more discussed on the chapter TCP, UDP and Controlling our Network Configuration (SSH, HTTP).
Configuring 1-to-1 NAT
Configuring 1-to-1 NAT has to be tought of bidirectional (steps 1 and 2) in the following example:
- traffic destined to the private IPv4 address (sometimes called Destination NAT) and
- traffic sourcing from the private IPv4 address (sometimes called Source NAT).
- the router needs to have the public IPv4 address at its disposal
Step 1.
set nat destination rule 10 destination address 88.113.241.57
set nat destination rule 10 inbound-interface eth0
set nat destination rule 10 translation address 192.168.0.5
Step 2.
set nat source rule 10 outbound-interface eth0
set nat source rule 10 source address 192.168.0.5
set nat source rule 10 translation address 88.113.241.57
Step 3.
set interface ethernet eth0 address 88.113.241.57/15
Verifying 1-to-1 NAT with show commands
Note worthy is that the destination translation doesn't need to translate the 25.0.0.2 source IP to anything.
Only the response source has to be translated.
show nat source translations and show nat destination translations
vyos@vyos:~$ show nat destination translations
Pre-NAT Post-NAT Prot Timeout
132.35.66.1 132.35.66.1 icmp 29
vyos@vyos:~$ show nat source translations
Pre-NAT Post-NAT Prot Timeout
132.35.66.10 10.0.10.8 icmp 29
vyos@vyos:~$
Port Forwarding
One answer to the visibility problem above is simple (tcp/udp) port forwarding. This is often an own category in consumer hardware. It means that only 1 port is forwarded from the public address to the private address (e.g. tcp/80 as in HTTP). It is often enough.
In the example below connections from the public Internet to address 88.113.241.57:80 (<ip-address>:<port>)are translated to the private IPv4 address of 192.168.0.5:80.
Configuring Port Forwarding
This port forwarding assumes that Many-to-1 NAT has been configured for the subnet 192.168.0.0/24. Thus only the port forwarding part has to be configured (directed to the destination private IPv4 address).
In the example below, HTTP connections (tcp/80) to the router's eth0 IPv4 address are translated to the private IPv4 address of 192.168.0.5:
set nat destination rule 10 destination port 80
set nat destination rule 10 inbound-interface eth0
set nat destination rule 10 protocol tcp
set nat destination rule 10 translation address 192.168.0.5
Verifying Port forwarding with show commands
show nat destination translations
vyos@vyos:~$ show nat destination translations
Pre-NAT Post-NAT Prot Timeout
88.113.241.57 192.168.0.5 tcp 104
vyos@vyos:~$
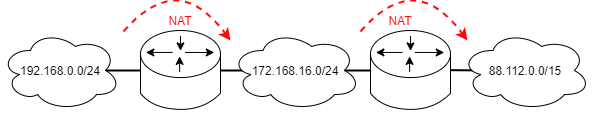
Carrier-Grade NAT
ISPs are fighting with the depleting IPv4 address space. This means that Carrier Grade NAT is sometimes utilized for mobile devices. This grotesque thing means that Private IPv4 addresses are translated to Private IPv4 addresses that are translated to Public IPv4 Addresses.
So multiple chained Network Address Translations are happening simultaneously.
Tip! You can go back to exercise E01 and inspect the traceroute section, if you did it from your home/mobile network!
I've noticed that some students have returned exercise repositories where this carrier-grade NAT is quite clearly happening in Finland.
This is not uncommon in consumer networks where multiple routers are installed in a chain with default settings. Reason typically being that the router/modem provided by the ISP is e.g. ADSL or Cable Modem without WLAN. Then a WLAN capable router is installed behind the actual ISP router/modem. Problems only arise when some service needs to be published behind the chained NATs to the Internet.
Continue to the Exercises
Back to the Schedule?
License
This course and its materials are written by Karo Saharinen and licenced by Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0) license.